Advocating Privacy and Data Protection for More Than a Decade And Still Fighting Resistance is Painful

I have been watching legal professionals disseminating personal data around the world. Feel my pain ? Why it especially matters? Because they are the ones advising others. They are the role model.
As the GDPR has now celebrating it’s 6 years and 4 years of enforcement, Here an exhaustive practical case law analysis of the importance of taking appropriate security measures and how things can go wrong.
I – Appropriate measures of security and data breach
I have been warning about the need for encryption when handling sensitive data. I have contacted the law society who have confirmed my requests as legitimate. Encryption is essential and WeTransfer is not an option. More secured tools are available; they are dangerously ignored. French Data Protection Authority CNIL has published recommendations not to use email to exchange personal data. ANSSI has published several warnings concerning the risks related to email exchanges.
It was first on Marsh 2021 that I received two separate emails, in two of my email addresses I had used with one of these French legals, a notaire (some kind of solicitor/notary). The emails as shown below, reproduced previous exchanges I had with the professional. It appears as a chain of communication, with a short sentence inviting to click on the attachment. Same kind of operations were repeated in June 2021.
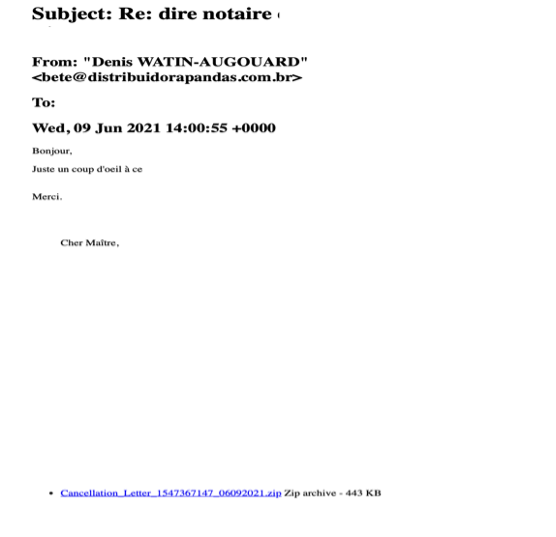
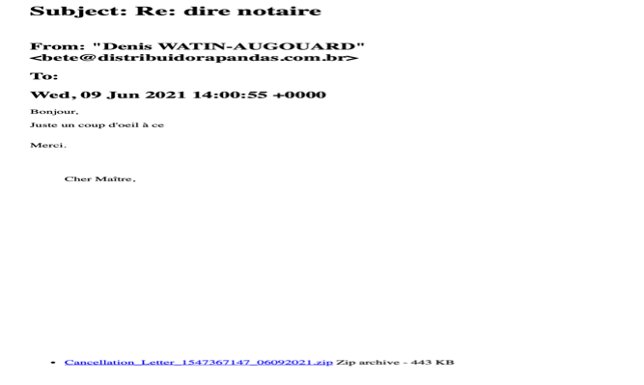
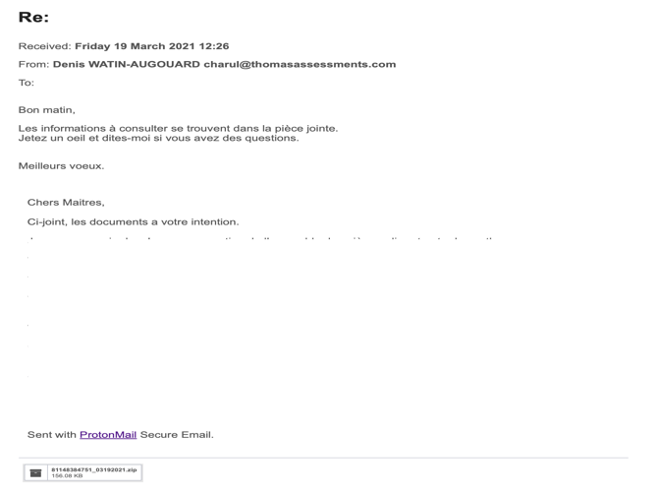
What Does that mean?
- Someone has been able to access to previous emails to this professional ;
- The mails were non-encrypted, despite my request to secure our exchanges ;
- These emails have fallen in the hands of cyber-criminals ;
- The cybercriminals have been to reproduce previous exchanges with the professional, including highly sensitive documents ;
- This to me is a data breach that should have been notified with 72 hours to the CNIL and without undue delay to data subject concerned if a serious risk was detected. I can’t see how this was not the case when a IBAN numbers, ID cards etc were exposed ;
- The phishing emails received contained a malicious zip file that has been analysed by an IT expert ;
- The attack is very similar to what has been described as a Qbot attack or Emotet. Several big companies such as Ikea, Fujifilm or JPS have been victim of these email chain attacks designed to extract financial data.
- Clicking on the zip attachment could infect the computer network to steal further financial information ;
- The email appears on a mobile device only showing the name of the professional to gain the recipient’s trust. It’s only by looking more closely that a different email address appears. Therefore, it becomes relatively easy to be trapped ;
- If I have received these 4 emails, there is a big chance I would not the only one ;
- Actually, this could be a larger scale attack of the platform used by notaires. Two other cases have been brought to my attention, one of them being the very respected lawyer representing me.
After I received the first emails, I sent several emails to the notaire on a different email address to check if they knew anything. I finally called them to understand what had happened. I was told by the big boss that he had no idea, had no care and probably have they been hacked just as it happens to many….
I then turned into the French Cyber Gendarmerie online, they told me it was a spam. But how a simple spam could reproduce my previous emails ?
Anxious about the data the cybercriminals had access to, I then send a request of information to the notaire trying to understand how they secured my data. They decided they needed an extra two months without justifying it. When I asked if they had a Data Protection Officer, they remembered than indeed all ‘notaires’ have an external mutualist DPO. Only in June did they notified the CNIL (data breach have to be notified within 72 hours to the CNIL and without undue delay to data subjects. My documents contained other people’s data breached as well. To my knowledge no data subject has been notified). From a document communicated by their DPO, last year the CNIL has requested some further information from them. So maybe after all this was not a simple Spam.
With the very slow progress with the notaire, I contacted a lawyer in Paris, Maître François-René Lebatard, who urged me to file a criminal complaint before all evidence would vanish. That was around June last year. The complaint is still under investigation.
Meanwhile, I contacted the CNIL that accepted to investigate my complaint. Here is their conclusion :
« Following the intervention of the CNIL, the data protection officer (DPO) of the firm, who was reminded of the obligations in force with regard to requests for access rights and the security of personal data, indicated:
…
They have, following the letter from Ms xxx of 20 March 2021 indicating that she had received fraudulent emails, questioned their IT service provider asking for a detailed expert report, investigations from which it appears that no data breach is proven, that the fraudulent emails received by Ms xxx took over emails which she was the sender, that they did not concern any email that the office would have sent to Ms xxx as a recipient and that no other office’s client had reported having received fraudulent emails.”
No further explanation on where these phishing emails came from. Case closed.
When back to our business with the notaire, I had to send him a legal document. I used Protonmail encryption. Again, he expected me to send it by email simple attachment. I had to remind him his DPO had mentioned they had a secure mean of document exchange. So even after the incident, was he still convinced exchanging data by simple email attachment ‘as usual’ is the way to go.
Now lets talk about the law firm involved in this case. A law firm advertising their international businesses. They exchangemassive amounts of documents by email attachment before discovering the joy of the free WeTransfer. Few law firms in Paris use WeTransfer because it’s free and convenient. I have tried my best to bring to their attention the risks paused by this tool. So, lets look deeper into that free WeTransfer.
- What’s wrong with the use of a free WeTransfer for a law firm ?
WeTransfer is a platform where users can upload their documents, receive a link with a password to send to their recipients.
- WeTransfer has been attacked several times in the past. Links have been intercepted or used in malicious spam ; According to WeTransfer, on June 16 and 17, file transfer emails were sent to unintended email addresses
“We have learned that a transfer you sent or received was also delivered to some people it was not meant to go to. Our records show that those files have been accessed, but almost certainly by the intended recipient. Nevertheless, as a precaution we blocked the link to prevent further downloads,”
- A phishing campaign observed by security researchers at the Cofense Phishing Defense Center targeting a wide range of high profile entities from industries such as media and banking was detected in july: “using WeTransfer notifications as surrogates for the run-of-the-mill malicious URLs usually employed in these type of attacks was recently detected while successfully bypassing email gateways developed by Microsoft, Proofpoint, and Symantec.”
- Again in August 2021, it is reported ‘New WeTransfer phishing attack spoofs file-sharing to steal credential’
- Free WeTransfer does not give the option of a Data Processing Agreement (DPA) required for any data processor used as by Article 28 GDPR ; Art 28-3 states : “Processing by a processor shall be governed by a contract or other legal act under domestic law, that is binding on the processor with regard to the controller and that sets out the subject-matter and duration of the processing, the nature and purpose of the processing, the type of personal data and categories of data subjects and the obligations and rights of the controller. “
- Data at rest is not encrypted and can be accessed ‘for technical purpose’ ;
- The balance of proportionality and obligations of article 32 GDPR – combined with Article 24 and 25, privacy by design – require to take account of the sensitivity of the data, balanced with the state of the art and the cost of the implementation, to take appropriate security measures, starting by encryption as reminded to the law firm Tuckers LLP fined by the UK ICO or by the Irish DPC fining Bank Of Ireland ; [the UK ICO referred to the “state of the art“, as ‘relevant industry standards of good practice including the ISO27000 series, the National Institutes of Standards and Technology (“NIST”), the various guidance from the ICO itself, the National Cyber Security Centre (“NCSC”), the Solicitors Regulatory Authority (“SRA”), Lexcel and ‘NCSC Cyber Essentials’. ‘
- Recital 83 on the balance of proportionality :
“In order to maintain security and to prevent processing in infringement of this Regulation, the controller or processor should evaluate the risks inherent in the processing and implement measures to mitigate those risks, such as encryption. Those measures should ensure an appropriate level of security, including confidentiality, taking into account the state of the art and the costs of implementation in relation to the risks and the nature of the personal data to be protected. 3In assessing data security risk, consideration should be given to the risks that are presented by personal data processing, such as accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed which may in particular lead to physical, material or non-material damage.”
- It happens that the French law society (CNB) that I have contacted has informed me of the existence of a secured platform lawyers can use for the transmission of their documents. Therefore no excuse to go to an unreliable free third party ;
- Additionally, WeTransfer uses AWS servers to store data, which is not without consequences with regard to the prohibition of data transfers to the US following the invalidation of the Safe Harbour then Privacy Shield based on the well-known ECJ decision in Schrems-II.
indisputable practicality
I have to say, the insistence of the law firm to use WeTransfer was not innocent. They had been warned their WeTransfer links would not be touched. Their insistence to refuse more secure options was not innocent and certainly part of their dirty strategy. They have been trying to pretend to communicate evidence that does not exist. Fortunately, another party took care to transfer their WeTransfer linked documents. The document listed was not there. They have yet not reacted on the missing documents requests several months later.
The same way have they ignored to respond to the requests concerning their appropriate security measures hiding behind attorney/client privilege. They were not asked to reveal their communications with their client.
It happens that their client who has initiated the various legal proceedings in France is based in China and to my knowledge, he exclusively uses his professional email address. He has even warned about his employer accessing his personal devices for inspection : … “Unfortunately my personal computer has been confiscated by xxx [the employer is a major communication provider with close tights with the government] for security reasons so can’t access personal mail till Monday. Because I used it for work in xxxx they have to take everything out of it including Windows 7 …”
Facing this abusive resistance, I had to turn into the CNIL. The CNIL requested the law firm to respond to my request. It was eventually clarified they used the free version of WeTransfer with no DPA. At least, they finally discovered they could use the secured CNB platform at their disposition. However, the password, a 6 single digit figures, was sent to all parties – including the notaire above –immediately following the link, using same channels. I personally find it hard to believe they could be that dumb. (I don’t think the CNB’s platform should allow such weak passwords. Dutch DPA has fined Transavia for poor personal data security allowing weak passwords ; French CNIL has been itself rather strict in their security requirements from Slimpay fined 180.000 €. )
Password strenght was highlited by ANSSI : « the length and complexity of a password remain basic criteria for assessing its strength.” The need for a strong password is crucial to ensure the security and confidentiality.
CNIL’s recommendations : “For the sake of clarity, the Restricted Committee notes that in order to ensure a sufficient level of security and satisfy the password strength requirements, when authentication relies solely on an identifier and password, the CNIL recommends, in its Decision No. 2017-012 of 19 January 2017, that the password have at least twelve characters – containing at least one upper-case letter, one lower-case letter, one number and one special character – or at least eight characters – containing three of these four characters – if it is accompanied by an additional measure such as, for example, the timing of access to the account after several failures (temporary suspension of access, the duration of which increases as attempts are made), setting up a mechanism to guard against automated and multiple attempts (e.g. a “captcha”) and/or locking the account after several failed login attempts. “ in CNIL SAN 2022-022 ».
- CNB’s recommendations : “Toutes les données envoyées par courriel ou transmises au moyen d’outils d’hébergement en ligne (Cloud) sont par conséquent vulnérables. Il s’agit donc de procéder à leur chiffrement systématique avant de les adresser à un correspondant ou de les hébergerLa transmission du secret (mot de passe, clé, etc.) permettant alors de déchiffrer les données, si elle est nécessaire, doit être effectuée via un canal de confiance ou, à défaut, un canal distinct du canal de transmission des données. Ainsi, si les données chiffrées sont transmises par courriel, une remise en main propre du mot de passe ou, à défaut, par téléphone doit être privilégiée. :
- ANSSI Guide de l’ hygiène informatique
In their letter they admited exchanging regularly with their client in China. This concerns massive amount of highly personal data for more than a decade, with no appropriate security measure. Their justifications? Well, China has voted the data protection regulation PIPL, so all is good !
They admit having been non-compliant for years before recently discovering the platform they had refused to use when first suggested.
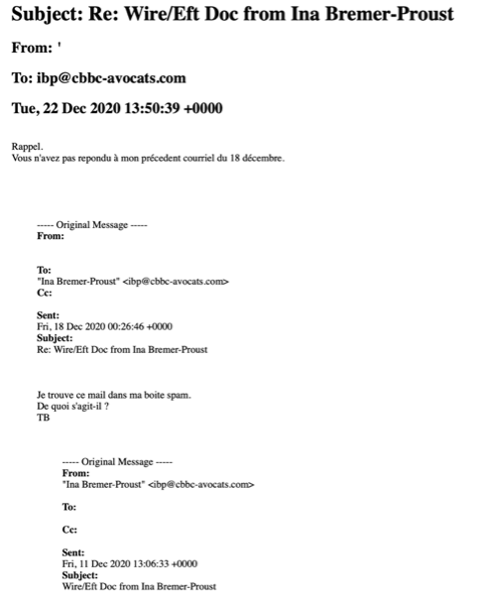
Again, this month, I received a fishing email from that law firm using a similar technic as shown below.
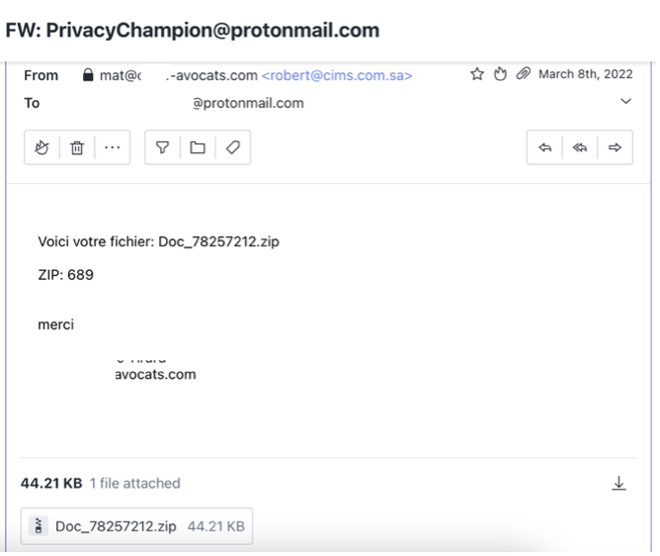
Previously, in December 2020 I had received another suspicious email from that same law firm they never clarified if it came from them or not
CNIL closed the case satisfied by these arguments without looking at :
- the question of long years of data transfers without any appropriate security measure ;
- the use of the free version of WeTransfer without DPA art 28 while they could at least afford the professional version offering better guaranties;
- use of the professional email address of the client and access by his employer
- CNIL accepted there has not been a transfer as the receiver is an individual to whom GDPR does not apply.
- resistance to reply to my requests, The CNIL did not care that the law firm rejected my DSAR for many years.
Here is a translation of CNIL’s decision – emphasises by me.
“Firstly, with regard to your difficulties relating to the exercise of the right of access to your personal data, XXXX, when questioned by the CNIL, indicated that this information was covered by professional secrecy. I confirm in this regard that, in accordance with the provisions of Article 23 of the General Data Protection Regulation (GDPR), the French legislator has, in Article 66-5 of Law No 71-1130 of 31 December 1971 reforming certain judicial and legal professions, provided for a limitation on the right of access. Under the above-mentioned article: “In all matters, whether in the field of counsel or in that of defence, consultations sent by a lawyer to his client or intended for him, correspondence exchanged between the client and his lawyer, between the lawyer and his colleagues with the exception for the latter of those bearing the mention “official”, the interview notes and, more generally, all documents in the file are covered by professional secrecy. ». [I don’t think I have ever questioned the confidentiality of their correspondences with their client]
Secondly, with regard to the supervision of the transfers of your data made by XXXX, in particular to China where the firm’s client resides to whom, according to your assertions [XXXX has XXXX clearly admitted doing so], your data would be sent, XXXX, questioned by the CNIL, indicates that there is no transfer strictly speaking.
I confirm in this regard that it follows from the ongoing discussions at the level of the European Data Protection Board (EDPB) that a transfer exists only if the personal data are transmitted to an importer located in a third country. However, since the client of the firm to which you believe your data is transferred cannot be qualified as a controller, joint controller or processor, the transmission operation cannot be qualified as a transfer of personal data outside the European Union.
Thirdly, as regards the security measures implemented by XXXX to guarantee the integrity and confidentiality of your data, that firm has on the one hand specified the security measures deployed in the context of the use of the “WeTransfer” tool and on the other hand indicated that it now uses the e-Sharing platform, developed by the National Council of Bars, whose technical characteristics as described in the firm’s response appear to meet the security obligations provided for in Article 5.1-f) of the GDPR. [Last WeTransfer link sent to me and other parties was last year. Before that for many years they exchanged via email attachment. They recognised I have been asking them – bothered them – to secure these exchanges due to highly sensitive data involved]
Regarding the facts alleged in your message of May 10, 2022 according to which the XXXX firm recently sent you the password through the same channel (email) as that used to send the link to the platform, and that this password contains only 6 characters, XXXXX was reminded of the elementary precautions recalled by the CNIL on these points.
In the light of these elements, I inform you to proceed to the closure of your complaint. »
Surprisingly, neither the law firm, nor the notaire care about the fraudulent use of their email addresses or name !
Although they admitted “Ms. xxx obviously benefits from the right to ask the data controller for access to personal data, the rectification or erasure thereof, or a limitation of the processing relating to the person concerned, as well as the right to object to processing and the right to data portability. These rights are however limited by the very purpose of the processing of personal data, namely the recognition, exercise or defense of legal rights (Articles 16, 17, 18 and 20 of the GDPR).”
The law firm pretended holding data indirectly collected. However, they forget that some of the documents have been directly collected to comply with the principle of ‘contradictoire’ or adversarial principal.
They pretend they are under no obligation to respond to my DSAR as I would already have knowledge of the information.
– Where personal data is not collected from the data subject, any available information as to its source :they argue this information is also covered by professional secrecy. Therefore, they would not be able to reveal all of their sources [expect use of private investigators]
“Under these conditions, if Ms. xxx actually wished to request such a copy, she is asked to specify the data or the processing operations to which her request relates, as Cabinet xxx cannot decently gather all of this information in just one months as required by the GDPR. [Did they requested an extended delay?]
Their justification on the use of WeTransfer is rather enlightening:
Indeed, WeTransfer has indisputable practicality –
They add “If the firm was able to effectively use this tool to transmit documents, during a well-defined and now over period, to Ms. xxx’s lawyer, to the notary, as well as to Ms. Xxx herself, it is recalled that the processing carried out here mainly concerned personal data relating to our client who has expressly consented to the use of this medium and has requested that it be use.” This is totally untrue. A legal case obviously involves exchange of personal data concerning various parties. How did CNIL not reacted to that is a mystery.
They have recognised using free WeTransfer in several occasions when they could have easily use alternative secure tools, ognoing my requests and the high sensitivity of the data: On February 3 and 20, 2020, October 14, 2020, January 14 and 22, 2021, January 29, 2021, December 9, 2021 and January 14, 2022.
They don’t despute my ‘numerous inquiries about WeTransfer’. It had to come to the CNIL’s attention for them to make ‘the necessary changes in order to comply with the GDPR and no longer use this service”.
II – On the question of regular long-term transfers to CHINA
The law firm is based in France. The litigation is initiated in France based on the French nationality of their client. The client is based in China. However, he travels around the world including in Europe where some of the exchanges have occurred and while in Europe, no doubt GDPR applied to these transfers. Data transfers via China where the email servers of the employer are located.
The law firm collect personal data from their client, from me directly in respect with the principal of adversarial, from the notaire, and I suspect from their communications, from private investigators. These documents are then forwarded to their client for observation. Then sent back to them. These will be used and reproduced to draft the court documents again exchanged between all parties including the client. Therefore, the law firm is data controller (see UK ICO cases of Tuckered LLP or Smith… ). Would the client be as well a data controller of the part of data he gathers, stores and processed? Possibly. In two cases, ECJ has considered individual as data controller : in the Facebook fan page admin case and in Jeowah’s Witnesses. [in ECJ Fashion ID “(A)s the Advocate General noted, […-] it appears that a natural or legal person may be a controller, within the meaning of Article 2(d) of Directive 95/46, jointly with others only in respect of operations involving the processing of personal data for which it determines jointly the purposes and means. By contrast, […] that natural or legal person cannot be considered to be a controller, within the meaning of that provision, in the context of operations that precede or are subsequent in the overall chain of processing for which that person does not determine either the purposes or the means”.
In Jehovah’s witnesses, C-25/17, the CJEU considered that a religious community of Jehovah’s witnesses acted as a controller, jointly with its individual members.]
The law firm argued that ‘The “transfers” in question are in no way regular and permanent but rather punctual and occasional, as much as respect for the adversarial process has made it necessary to communicate the documents in the file. Moreover, strictly speaking, there is no transfer outside the European Union at the initiative of xxx since it is the recipient of the data who imports the data because he is domiciled outside the European Union. And it should be remembered that the GDPR does not apply to natural persons not residing in the European Union.”
Can we still talk about ‘ponctual and occasional’ for something that has last 11 years ?! Massive amount of highly personal sensitive data have been exchanged refusing the special request to use encryption rejected.
Their argument is that the transfers almost exclusively concerned data obtained indirectly through the lawyer., the notary or the client. This is not exact as some of the data was directly collected.
Knowing that several litigations initiated since 2011 involving different jurisdictions in France, it’s difficult to admit these heavy volume of data exchanges were ‘ponctual’ (3 court of appeals, 4 other jurisdictions, several notaires, huissiers, or Avoués were involved each time data has been sent with no care)
In any case, their communications between the law firm and the notaire are not confidential Article 14 paragraph 5, d). – in contrary I should have been in copy on all of them
- Concerning Chinese employers practice, here is report by Politico :
“A case filed by one of Huawei’s former managers at its European headquarters in Düsseldorf takes aim at another pitfall for the company: Its respect of European privacy rules.
Specifically, it opens up questions about whether Huawei is putting data at risk of slipping into the hands of Chinese state surveillance and intelligence operations. It also raises questions about whether Europe will sharpen its tone with China on sensitive data privacy matters — after years of focusing its ire on Silicon Valley’s giants and U.S. state surveillance.
A judge ruled March 5 that Huawei was in breach of European privacy law when it failed to comply with the former manager’s request to view the data the company had kept on him.”
- Ultimately, non-compliance with GDPR is a criminal offense :
Art. 226-16
The fact, including negligence, of carrying out or having carried out processing of personal data without having complied with the formalities prior to their implementation provided for by law is punishable by five years’ imprisonment and a fine of 300,000 euros.
Le fait, y compris par négligence, de procéder ou de faire procéder à des traitements de données à caractère personnel sans qu’aient été respectées les formalités préalables à leur mise en oeuvre prévues par la loi est puni de cinq ans d’emprisonnement et de 300 000 euros d’amende.
Art. 226-17
The fact of carrying out or having carried out a processing of personal data without implementing the measures prescribed in Articles 24, 25, 30 and 32 of Regulation (EU) 2016/679 of 27 April 2016 or in 6 ° of Article 4 and Articles 99 to 101 of Law No 78-17 of 6 January 1978 cited above is punishable by five years’ imprisonment and a fine of 300,000 euros.
Le fait de procéder ou de faire procéder à un traitement de données à caractère personnel sans mettre en oeuvre les mesures prescrites aux articles 24, 25, 30 et 32 du règlement (UE) 2016/679 du 27 avril 2016 précité ou au 6° de l’article 4 et aux articles 99 à 101 de la loi n° 78-17 du 6 janvier 1978 précitée est puni de cinq ans d’emprisonnement et de 300 000 euros d’amende.
Previous related CNIL’s decisions
For reference, here are previous similar cases involving the questions of security measures
- Slimpay, lack of measures of security article 32, without the need to prove any illegitimate access to the data :
“95. The Restricted Committee then notes that the accessible data (title, surname, first name, e-mail address, postal address, telephone number, BIC/IBAN) make it possible to obtain very precise information on the persons concerned by revealing their identity and their contact information. In addition, specific data are in question when some relate to financial information. The fact in particular that the IBAN appears is not insignificant. As the Banque de France indicated in its book “Payments and market infrastructures in the digital age”, IBANs are “sensitive” payment data (in the ordinary sense of the term) because they can be used to commit fraud. . The European Data Protection Board describes this type of data as “highly personal”. The Restricted Committee considers that the company should have exercised particular vigilance with regard to securing such data, which may be reused by unauthorized third parties, thus harming the persons affected by the data breach. These are, for example, exposed to a risk of identity theft or phishing (or “phishing”, i.e. the sending of fraudulent letters for the purpose of obtaining data) when their full identity, associated with their email address for many, was freely accessible. thus prejudicing the persons affected by the data breach. These are, for example, exposed to a risk of identity theft or phishing (or “phishing”, i.e. the sending of fraudulent letters for the purpose of obtaining data) when their full identity, associated with their email address for many, was freely accessible. thus prejudicing the persons affected by the data breach. These are, for example, exposed to a risk of identity theft or phishing (or “phishing”, i.e. the sending of fraudulent letters for the purpose of obtaining data) when their full identity, associated with their email address for many, was freely accessible.
“68. The Restricted Committee considers that the absence of proof of fraudulent use of the data has no impact on the characterization of the breach of the security obligation. Indeed, the risk of fraudulent use of personal data was real, independently of the cases of fraud, insofar as the data of many people were made accessible to unauthorized third parties. The absence of proven harm to the persons concerned does not affect the existence of the security defect, which constitutes the breach of Article 32 of the GDPR.”
- The French DPA (CNIL) imposes a 3,000 euros fine on a doctor for failing to comply with the security obligation, due to the free access on the web of his patients’ health data. CNIL recalls its own guidelines on Personal Data Security recommending encryption as a standard security measure. Similarly, the Practical Guide for Physicians encourages physicians to encrypt their patients’ data with suitable software.
Transmitting unsecured emails: the restricted training points out that it also emerges from the hearing of December 17, 2019 that “Mr. […] had also not taken care to encrypt the data contained in his personal laptop, considering that encryption slows down the execution of applications too much (medical file, image visualization tool).
26. In the absence of encryption, the medical data contained in that computer’s hard drive were readable in plain text by any person taking possession of that device (for example, as a result of its loss or theft) or by any person who unduly entered the network to which that computer was connected.”
In its guidance The security of personal data, the CNIL recommends providing encryption means for nomadic workstations and mobile storage media (laptop, USB keys, external hard disk, CD-R, DVD-RW, etc.), for example via the encryption of the hard disk in its entirety when the operating system offers it, file-by-file encryption or the creation of encrypted containers (file likely to contain several files). Similarly, the Practical Guide for Physicians invites physicians to encrypt their patients’ data with appropriate software.
- The French DPA (CNIL) fined a mobile operator €300,000 for failing to respect customers’ right of access and right to object by not responding to their access requests in a timely manner and sending them marketing messages despite having been notified of their objection to such processing.
- The French DPA (CNIL) imposed a € 2250000 fine on Carrefour France for several violations of the GDPR and French data protection law. These include : excessive data retention periods, incomplete and unclear information on data processes, lack of proper answer to data subjects’ requests, security breaches and illicit use of cookies.
- The CNIL also referred to a decision n°423559 by the French Supreme Administrative Court (Conseil d’Etat) which allowed for such sanctions, even if the violation had been corrected. (NESTOR)
Other cases in the EU
- A hospital in Sweden received a fine of 150k EUR because it was sending medical records via email to patients and referring hospitals, unencrypted.
That was a GDPR security issue, in direct breach of art 5 (1)(f) GDPR (principle of security) and art 32 GDPR (security of processing).
Email is an obsolete communication mechanism, start using encrypted document sharing solutions, with strong authentication! - The Romanian DPA issued a fine of approximately €1000 on a law firm for disclosing a case file with the personal data of one of its clients on an external WhatsApp group with other lawyers, in breach of Articles 6, 5(1)(a), 5(1)(b), 5(1)(c), 5(1)(f) and 5(2) GDPR.
- Hungarian DPA fines Lawyer € 835 for unauthorized transmission of a confidential document to two unauthorized third parties.
The data subject lodged a complaint with the DPA concerning the unlawful disclosure of his personal data.
The recipient of the fine acted as a lawyer for a company that was in litigation with the complainant.
In his complaint, the concerned party alleged that the respondent had improperly and without cause disclosed to two other parties in the case “highly confidential information”, which was a private letter to the President and Vice-President of an unnamed company.
- The view that the sending of an unencrypted e-mail might violate Art. 32 GDPR is also the opinion of the Data Protection Authority of North Rhine-Westphalia (DPA NRW), which says the following on its website:
“The communication by e-mail requires at least the transport encryption, as it is offered by the considerable European providers by default. … It must be taken into account that in the case of transport encryption the e-mails are available on the e-mail servers in plain text and can basically be viewed. In the case of particularly sensitive data (e.g. account transaction data, financing data, health status data, client data from lawyers and tax consultants, employee data), transport encryption alone may not be sufficient“. (DPA NRW, Technical Requirements for Technical and Organizational Measures for E-Mail Sending, available here in German).
With special thanks to the experts who have offered me their assistance on this matter :
- David Flint, Commercial Law Consultant at Inksters; Visiting Professor at Creighton University School of Law.
- Peter Stephenson, PhD, CISSP, FAAFS Writer, researcher and educator in cyber criminology and cyber jurisprudence.
- Alexandre Blanc Cyber Security – vCISO – ISO/IEC 27001 and 27701 Lead Implementer – best Cyber Risk Communicator of 2019 and 2020 – MCNA – MITRE ATT&CK – LinkedIn Top Voice 2020 in Technology – Cyber Sentinel Award 2020-21 – Speaker